The Escalating Threat of Robocalls
The urgent need for advanced digital identity to combat a pervasive problem that is predicted to get worse.
Robocalls have evolved into a pervasive and disruptive problem, largely due to the rapid advancements in telecommunications and information technology. These technological leaps have significantly reduced the costs associated with telecommunications and computing infrastructure, making it cheaper and easier to place automated calls.
While these advancements have brought many benefits, they have also inadvertently fueled the rise of robocalls, creating new challenges for individuals, businesses, and regulatory bodies alike.
VoIP/SIP technology, while offering cost-effective solutions for legitimate communication purposes, has also been exploited for unlawful activities, allowing perpetrators to operate with a high degree of anonymity.
Unlike traditional telephony systems, VoIP/SIP makes it incredibly cheap to place massive volumes of calls, often without incurring significant costs even if the calls go unanswered. This has emboldened scammers and unscrupulous telemarketers to utilize robocalls for their nefarious purposes.
One of the most common tactics employed by robocallers is "telephone number spoofing," which involves manipulating the caller ID to display a telephone number that is not legitimately owned and/or controlled by the entity originating the call.
While there are ethical and lawful use cases for spoofing, such as a pharmacy displaying a local branch number for prescription notifications, illegal spoofing is rampant. Bad actors often impersonate legitimate organizations to deceive call recipients, potentially leading to fraud, identity theft, and other harmful consequences.
The Challenge of Trust in VoIP
Voice over Internet Protocol (VoIP) has revolutionized business communications with its cost-effectiveness and scalability. However, the inherent anonymity of VoIP systems has also enabled the rise of unwanted robocalls and phone number spoofing, eroding consumer trust. Unlike traditional SS7/TDM networks, VoIP lacks end-to-end authentication, making it difficult to verify the identity of callers.
While telephone numbers (TNs) serve as a form of identity, they are not reliable in the long term. Consumers change numbers frequently, and organizations, especially those involved in telemarketing and tele-sales, often rotate TNs rapidly. This "hyper-rotation" can be used to circumvent regulations and even perpetrate scams.
The STIR/SHAKEN framework has emerged as a significant tool in combating caller ID spoofing. By using digital signatures to authenticate call origins, STIR/SHAKEN verifies that the caller is authorized to use the displayed number. The framework also assigns attestation levels to calls, indicating the level of trust associated with the caller ID.
Despite its benefits in reducing robocalls and improving trust, STIR/SHAKEN has limitations. It primarily focuses on authenticating networks to TNs, not on verifying the organizations behind the calls. This leaves a gap in accountability, especially for organizations that frequently change numbers or engage in questionable calling practices.
Brand Impersonation and the Rise of Deep Fakes
Brand impersonation is another deceptive tactic used by robocallers, where they explicitly or implicitly claim to represent a legitimate company or organization. This unethical and often illegal practice erodes consumer trust and can cause significant damage to the impersonated brands.
The emergence of AI-generated deep fakes has further exacerbated the problem, making it increasingly difficult to distinguish between real and fabricated content. Deep fakes can create highly realistic videos or audio recordings that appear to show someone saying or doing something they never actually did. This technology can be used for malicious purposes, such as blackmail, extortion, or reputational damage.
While telephone numbers (TNs) serve as a form of identity, they are not reliable in the long term. Consumers change numbers frequently, and organizations, especially those involved in telemarketing and tele-sales, often rotate TNs rapidly. This "hyper-rotation" can be used to circumvent regulations and even perpetrate scams.
Voice Cloning and Conversational AI: New Tools for Deception
Voice cloning technology, powered by advanced machine learning algorithms, has made it possible to replicate a person's voice with remarkable accuracy. This technology has various legitimate applications, such as recreating voices for movies, video games, or personalized virtual assistants. However, voice cloning can also be misused for malicious purposes, particularly when combined with conversational AI.
Conversational AI enables machines to engage in natural-sounding conversations with humans, mimicking human-like responses and interactions. While perfectly replicating an individual's speech patterns remains challenging, conversational AI can create highly believable interactions, especially when programmed with personal or contextual information.
This creates new opportunities for deception, as bad actors can use voice cloning and conversational AI to impersonate individuals or organizations with greater credibility.
The Ethical Concerns of AI Misuse
The rapid advancements in AI technology, particularly in voice cloning and conversational AI, have raised significant ethical concerns. The potential for misuse is substantial, as bad actors can exploit these technologies for fraud, deception, and manipulation. The ability to create highly realistic synthetic voices and engage in believable conversations opens up new avenues for social engineering attacks, phishing scams, and other forms of online fraud.
Generative AI, which can create realistic websites, emails, and messages, further amplifies the threat. When combined with data scraping techniques, generative AI can be used to train conversational AI systems to deliver highly personalized and contextually relevant information, making the deception even more convincing. This raises serious concerns about the potential for large-scale manipulation and the erosion of trust in online communications.
Combating Unlawful Communications With Advanced Digital Identity
To combat the growing threat of robocalls and AI-driven deception, a comprehensive approach is needed, encompassing technologies, policies, procedures, and methods that work together to create a "Trusted Communications" framework.
Key components of this framework include Consent Management, UI/UX design, Digital Identity, Know Your Everything (KYX), Monitoring, Authentication, and Validation. While these tools can be implemented individually, a more effective approach is to integrate them into a cohesive system.
The Need for Organizational Identity and Proof-of-Life ID
Advanced digital identity management is a crucial tool in the fight against unlawful communications. As mentioned, current methods rely heavily on network and telephone number identification, such as the STIR/SHAKEN framework.
STIR/SHAKEN authenticates calling numbers and networks, providing a degree of protection against spoofing. However, it does not address the issue of organizational identity or provide direct traceability to the organizations responsible for the calls.
To overcome these limitations, two key areas of focus for next-generation digital identity are:
Organizational Identity
This involves establishing a verifiable link between a communication attempt and the organization responsible for it. This enables non-repudiation, meaning that organizations cannot deny their involvement in a call or message. It also provides a mechanism for accountability, allowing for the identification and prosecution of bad actors. Advanced implementations of Organizational Identity could even enable real-time call processing, allowing for the blocking or flagging of suspicious calls based on the identity of the originating organization.
Generative AI, which can create realistic websites, emails, and messages, further amplifies the threat. When combined with data scraping techniques, generative AI can be used to train conversational AI systems to deliver highly personalized and contextually relevant information, making the deception even more convincing.
Human vs. Bot (Proof-of-Life ID)
This involves determining whether a communication attempt originates from a real human or a synthetic voice (bot). This is a crucial distinction, as “bot-generated” calls and messages are often used for malicious purposes. A Proof-of-Life ID could be used to filter out “bot-generated” communications or to provide users with additional context about the nature of the communication.
The implementation of organizational ID would likely involve assigning a unique ID to each organization and mapping it to their associated TNs. This data would be shared between telecom service providers, initially on a non-real-time basis for post-call analysis and accountability. Eventually, real-time sharing could enable more proactive call processing and reduce false positives in analytics engines.
The benefits of organizational ID are numerous:
Traceability and Accountability: Linking calls to specific organizations ensures that bad actors can be identified and held accountable.
Enhanced Trust: Consumers can have greater confidence in calls from verified organizations.
Improved Analytics: Real-time organizational ID data can improve the accuracy of analytics engines, reducing false positives and negatives in spam detection.
Support for Branded Calling: Organizational ID is a crucial foundation for branded calling, which provides a richer and more trustworthy caller ID experience.
Verification and KYC Integration for Enhanced Trust
Reliable authentication and validation are essential for both Organizational Identity and Proof-of-Life ID. The use of cryptographically verifiable credentials and blockchain technology is recommended to ensure the integrity and trustworthiness of these digital identities. Additionally, these digital identities should be integrated with Know Your Customer (KYC) onboarding and monitoring practices to further enhance trust and accountability.
Organizations would be required to register their telephone numbers and declare whether they are associated with human or bot activity. KYC monitoring would then be used to verify the accuracy of these claims and identify any false or misleading information. This would help to ensure that organizations are held accountable for their communication practices and that consumers can trust the information they receive.
UI/UX Considerations for User Transparency
In addition to technical solutions, it is also important to consider the user experience when designing and implementing digital identity systems. UI/UX enhancements should focus on providing users with clear and transparent information about the nature of their communications.
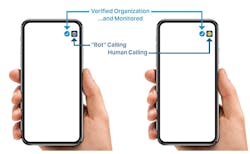
Simple visual cues, such as icons or checkmarks, could be used to indicate whether a call or message is from a human or a bot. This would empower users to make informed decisions about how to engage with different types of communications and help to build trust in legitimate businesses and organizations.
Organizational Identity and Branded Calling
Branded calling represents a significant step forward in caller ID, providing a more visually appealing and informative display for consumers. This enhanced UI can include the company logo, call reason, and other verified information, increasing consumer trust and engagement (see Figure 1). There is inherent trust in branded calls, as the businesses involved are assumed to be fully vetted, and the calls associated with these businesses are assumed to be authenticated and validated as genuinely from the organization.
However, branded calling and organizational identity may each stand alone as separate means of facilitating trust in B2C contact. For example, non-branded calls, displaying a "Verified Organization" indicator can enhance trust and transparency. This allows organizations to benefit from increased accountability and consumer confidence without the added cost of branded calling.
Conclusion: A Multi-Faceted Approach to Secure Communications
The escalating threat of robocalls and AI-driven deception demands a multi-faceted approach to secure communications. Advanced digital identity solutions, such as Organizational Identity and Proof-of-Life ID, coupled with robust verification, KYC integration, and user-centric UI/UX design, are crucial for combating unlawful practices and protecting consumers.
Introduction of a cryptographically verifiable organizational ID is a crucial step in establishing a more trustworthy and accountable communication ecosystem. By providing a persistent and reliable identifier for organizations, this new data element will enhance transparency, deter bad actors, and empower consumers to make informed decisions about the calls they answer.
By implementing these measures, the industry can foster a more transparent, accountable, and trustworthy communication environment, empowering users to engage with confidence and mitigate the risks associated with malicious actors.
About the Author

Gerry Christensen
Gerry Christensen is Principal Consultant with Wireless Waypoint, which provides consulting, management, advisory and expert services for the information and communications technology industry. Core competency areas are switching, signaling, and related technologies and solutions. Practice areas include strategy, business development, fractional and interim management. This includes legacy telecom/IT as well as emerging business models and ecosystems, network infrastructure, VoIP networking and IP based services, operational and business support systems.
For more information, and to connect with him, visit www.linkedin.com/in/gerrychristensen/.