Latest from Home
Recent updates include notices from Theorem, OpenVault, and Broadband Forum. Visit https://isemag.com/category/safety/telecom-covid-19-network-impact-wireless-wireline/ often to find more COVID-19 Impact Updates.
The Evolving Culture of Cybersecurity: How Well Do You Know Your Network?
Mitigating Security Risks Beyond the Firewall
Pre-COVID, enterprises would create a "security perimeter" around the network in their offices, such as a firewall and smart switches and network elements to control the environment. Now, we’re in the midst of the most massive security shift since the dawn of the internet. Companies must face the security realities of remote work — and do it fast.
Since the onset of COVID-19, you’ve likely run into security measures that were never an issue before moving to remote work. Simultaneously, companies are restructuring budgets to compensate for economic impacts due to the pandemic. Investing in growth right now is a tricky business, but the one place where companies cannot afford to compromise is their security systems.
BREACHES ARE NO JOKE
Cybercrime costs the global economy $2.9 million every minute. The average damage to a business in the United States after one data breach is $8.64 million. Let’s say you have the cash flow available to survive the legal costs and damage to your business. The revenue loss would be a massive problem — but it wouldn’t be the only one.
While your business works to repair compromised systems and return to productivity, you will have to address the data breach notification legal requirements mandated by each state and country. Once you achieve compliance, you need to regain your customers’ trust and campaign to restore your business’s image.
The alternative? Prevention and mitigation strategies.
By taking a survey of your current security measures, you can identify holes or fractures lurking in your system before any breach.
HOW SECURE IS YOUR NETWORK RIGHT NOW?
Consider your network before the pandemic. You likely had security tools, tactics, and policies in place to monitor unauthorized intrusions. Your network administrator assured you that the most sophisticated firewall is churning out top-notch encryption methods to prevent breaches. There was an impenetrable perimeter around your network.
But what happens when companies ask their employees to work from home due to a global pandemic? The secure environment you’ve worked so hard to build isn’t as helpful when 350 computers from 350 different external local area networks (LANs) are suddenly fraternizing with your otherwise stable system.
• Will it hold up?
• How well do you know this complex network?
• Can your systems withstand an extreme variation of protocol due to the present-day challenges?
SIGNIFICANT OBSTACLES
These are today’s most significant obstacles to securing your data.
Problem 1: The Rapid Transition to Remote Work
Most management teams were not prepared for remote work when forced into distributed teams earlier this year. Critical data is in one location, and employees are scattered about in others. When everyone is no longer under the same roof, things get complicated. With many employees now working 100% from home, your network is only as secure as theirs — if you don’t incorporate the potential risks of home offices in your current incident response plan (IRP).
This is the most considerable security transformation we’ve ever seen, and companies are vulnerable. Most large enterprises used to allow occasional work from home — maybe even a day per week — but are now scrambling to get the necessary tech to their employees for safe, long-term remote work.
Problem 2: Employees With Insecure Networks
If you work for a company that’s not technically oriented, your employees might require significant education on safe remote work practices. Your team needs to understand the risks to company security at home or on the go.
You need to take action at the network level to protect your company in terms of home network administration and employee machines to prevent exposing open web application ports to other devices on the same network. You don’t know anything about the network administration of a random coffee shop, for example. How do you trust that the coffee shop has adequate network security? You can’t.
Problem 3: Outside Users Who Compromise the System
The same applies to home WiFi networks.
• What about an employee’s teenage son who’s downloading suspicious bit torrents?
• Malware can start scanning for open ports on the machine.
• Using remote code execution, curious hackers could start poking around on anything you may be developing.
• They could even potentially get access to credentials for sensitive information.
• The entire system could be compromised.
To exacerbate the situation, a lot of local development is created with debugging mode on — meaning that the source code for a web application is often exposed in a more readable format with a source map. A hacker could see what you’re working on, identify its source code, and even gain credentials to a critical program. If your team is working on valuable IP (intellectual property), this is a risk you can’t afford.
InvisiLight® Solution for Deploying Fiber
April 2, 2022Go to Market Faster. Speed up Network Deployment
April 2, 2022Episode 10: Fiber Optic Closure Specs Explained…
April 1, 2022Food for Thought from Our 2022 ICT Visionaries
April 1, 2022THE SOLUTIONS
In this newly distributed environment, it’s critical to protect yourself from social engineering tactics the same way you protect your devices from malware.
There are 2 straightforward measures you can take to protect your network.
The first is PHYSICAL SECURITY.
1. Establish Practices for Physical Security
Make sure your team always uses their company-issued devices, and that hard drives are encrypted. You also want to make sure that an attacker would need your fingerprint or password to get access to any data. Two-factor authentication and biometric data requirements might require a few extra seconds to log in and get to work, but they’ll vastly slow down hackers.
Two-factor authentication—commonly known as 2FA—is a security method that requires additional steps to verify a person’s identity before unlocking access. If you’ve ever received a text message with a code to log in to your bank account, then you’ve used two-factor authentication. Other options include a push notification to a mobile device or an authentication app that provides a code. But this approach may not improve security as much as you think. Because the code is something you know, like your password, it can compromise your security if it’s swiped. For protection of sensitive accounts, you may want to install hardware security keys on laptops, such as YubiKeys, which employees must press to populate a login form with code.
On the other hand, biometric data generally refers to a fingerprint or facial recognition, such as Touch ID and Face ID on Apple devices. While biometric authentication is an excellent way to verify identity, you must ensure that this data is stored locally and not sent to an external server, where it can be compromised and used by hackers.
2. SET UP A VPN
The second tactic is to utilize a VPN (virtual private network) to create an additional security layer.
Some VPNs will — in essence — fully isolate you from your home network or any other outside network like a coffee shop or an airport. Other VPN options allow you to be a member of both at the same time. Before you choose, it’s essential to know what you want and expect from your VPN package. Factors to consider include security measures, privacy, speed, reliable connections, user-friendly interface, multiple servers, and cost. To prevent misuse of VPNs, you may also want to consider using Zero-Trust Network Access Technology (ZTNA), which uses microsegmentation and isolation to ensure stricter user-access control.
Some companies question whether they need a full VPN or if a secure cloud service like AWS (Amazon Web Services) is enough. VPNs are the vanguard of safe and effective remote work, but cloud-based servers have been on the rise in recent months. The hassle of daily server maintenance is outsourced to a third-party who does most of the heavy lifting. Clouds are also more compatible with mobile apps. But, they can’t necessarily guarantee security.
A CLOUD SERVICE IS NOT A SECURITY MEASURE
This accelerated shift to cloud services may eventually transition what is known as Secure Access Service Edge. Companies will need to strengthen their identity and access management tools and use automated monitoring and remediation capabilities to prepare for any identity-related threats on the cloud.
Not all cloud-based services are created equal in their level of security. Companies should look for services with an established track record of preventing breaches and skillfully handling any attacks they’ve suffered. AWS uses a shared security model. They are responsible for part of the security and delegate the rest to the client. As threats continue to evolve at a rapid pace, the use of automated systems to streamline cloud security management may also become highly valuable. For example, tools like Cloud Security Posture Management help companies identify and remediate risks through security assessments and automated compliance monitoring, while an extended detection and response system monitors and collects activity data from endpoints to identify possible cyber security threats.
It’s crucial to understand that just adopting a cloud is not a security solution. Leaders should also consider requiring multi-factor authentication for logging into their cloud services—not only for their hardware devices, as discussed above.
SO VPN? CLOUD SERVICE? OR BOTH?
Though both VPNs and clouds have proven to be successful in their arenas, deciding factors often come down to budget. A company choosing to adopt a VPN needs to invest quite a bit more in infrastructure and security personnel to administer the system adequately. Secure cloud services might be more practical for smaller companies without these resources.
Despite the debate, there doesn’t need to be a dichotomy between VPNs and cloud services. You just have to choose what’s best for your company.
FINDING THE RIGHT TEAM
Working from home is the new norm. The most crucial element is a security team with the skills and expertise to recommend the right measures and tools. Without a thorough evaluation, your company is living dangerously in the Wild Wild West of a distributed environment.
About the Author:
Theorem is an innovation and engineering firm that builds custom software for companies making bold bets to stay ahead. Theorem’s global cross-functional development teams drive technology, process, and cultural transformation.
Mikaela is an experienced marketing executive with a history of working in technology, consumer products, healthcare, and professional services. She has led marketing efforts for several consulting agencies by scaling up their internal capabilities to attract large enterprise organizations as customers. She is especially skilled in digital marketing, brand innovation, and business development and holds a master’s degree in technology commercialization from The University of Texas at Austin. At Theorem, Mikaela is responsible for engaging prospective clients and manages all outbound marketing efforts. In her free time, she frequently enjoys talking about emerging technologies over a glass of ginger turmeric tea and an Omaha poker game.
OVBI: COVID-19 DROVE 51% INCREASE IN BROADBAND TRAFFIC IN 2020
OpenVault: Average consumption approaches one-half TB
Traffic on broadband networks rose by more than half and average broadband usage approached one-half a terabyte at the end of 2020, according to the Q4 2020 OVBI (OpenVault Broadband Insights) report issued recently by OpenVault, a market-leading source of SaaS-based revenue and network improvement solutions and data-driven insights for the broadband industry.
Per-subscriber average data usage for 4Q20 was 482.6 GB per month, a 40% increase over the 344 GB consumed in 4Q 2019 and a 26% increase over the 3Q20 average of 383.8. At the same time, broadband providers saw subscriber increases of 6.5%, creating a net effect of 51% more broadband traffic. 4Q20 median usage rose 54% year-over-year, to 293.8 GB per month from 190.7 GB in 2019.
In addition to record growth, the 4Q20 OVBI also shows general trends that became evident during the pandemic. OpenVault data shows that once average monthly usage jumped almost 47% in April of 2020, trend lines of rising and falling usage almost uniformly followed pre-pandemic norms, albeit at this new, higher level. The report also shows the continued growth of upstream usage; in 4Q20, upstream consumption was 31 GB/month, an increase of 63% over 4Q19.
The 4Q20 report also spotlights the continued effects of power users on broadband networks. Among the most recent data:
• 14.1% of subscribers now consume more than 1 TB of data per month. That represents a 94% rise — 61% in 4Q20 alone — from the 4Q19 average of 7.25%.
• Extreme power users, those consuming more than 2 TB per month, increased by 184% year over year, from 0.76% in 2019 to 2.2% at the end of last year. Similar to the 1 TB data, 120% of that increase occurred between Q320 and Q420.
• Providers offering unlimited, flat-rate billing packages saw nearly 30% more power users than those with usage-based billing plans.
• More than half (53.6%) of all subscribers now consume more than the former power user threshold of 250 GB per month.
"The impact of the COVID-19 pandemic was complete and has forever changed broadband usage patterns," the report notes. "Network operators now must contend with significantly higher average bandwidth usage, with implications for both network management and revenue. Network operators should evaluate all network management options to ensure they deliver the best customer experience while maximizing profitability."
The entire report is available at http://openvault.com/complimentary-report-4q20/. OpenVault also provides continuously updated broadband consumption figures at https://openvault.com/trusted/.
About the Author: OpenVault and OpenVault Europe GmbH are market-leading sources of broadband technology solutions and data-driven insights into worldwide broadband consumption patterns. The companies’ cloud-based, SaaS solutions and tools help service providers optimize network performance, increase revenue and improve subscriber satisfaction. OpenVault and OpenVault Europe aggregate and analyze the resulting market data to provide unparalleled granular views of consumer usage that can be used to anticipate residential and business broadband trends. For more information, please visit openvault.com.
Connected Home Device Boom Demands User Services Focus in 2021
Increasing demands for faster, more efficient and more reliable ways to manage connected devices will make 2021 the year of service and device lifecycle management, according to open broadband standards development organization, the Broadband Forum. Broadband Forum’s User Services Platform (USP) standard offers related data models and the communication protocol to master such needs.
The rapid growth of internet connected devices in the home has accelerated owing to the increased amount of time people have had to spend at home during the pandemic. A new major study recently published highlighted that the number of installed connected devices is expected to rise by a further 70% by 2025. Similarly spending on smart home systems is expected to rise to a projected $157 billion worldwide by 2023, for example.
"Given that we expect the rapid rise of connected devices in the home to continue this year and beyond, our recent survey report emphasized that the number of users and vendors utilizing USP continues to increase too," said Broadband Forum Chairman of the Board and Co-Director of the Broadband User Services Work Area John Blackford. "The Broadband Forum will be responding to this focus on user services by making regular updates and developments to the USP. We are already working on the next versions of the Device:2 root data model (TR-181) and the USP standard to add new functionality and further solidify USP as the go-to interoperable ecosystem for the Connected Home."
As a reference implementation, the Broadband Forum’s Open Broadband — USP Agent (OB-USP-Agent) project aims to increase the number of new USP deployments per year. By providing a functional and free open source implementation of the USP standard, interested parties can easily understand USP, try it out in a USP deployment or use it as a foundation for their own protocol implementations. Jointly developed by device and infrastructure vendors as well as operators it serves as a golden standard and helps prove the quality of USP and supports further standard developments. Impressively, the number of new participants in the OB-USP-Agent project team has risen by more than 60% in the last 12 months.
"Because it evolves the success story of TR-069, builds on a decade of device management experience, and puts open standards into practice, the USP reference implementation is really a building block for vendors to use," said Axiros CEO Kurt Peterhans. "Its latest developments will allow vendors such as ourselves to accelerate and to bulletproof their own USP solution developments. This will help unlock the potential of the Connected Home and enable operators to capitalize on the IoT market."
With an increase in the number of connected devices comes a rise in the importance of remote management and updates for devices and Wi-Fi management. New standards in the home like Wi-Fi 6, coupled with new technologies extending IoT capabilities like 5G and gigabit-fiber deployments, are adding to both the challenges and complexities for the service provider in the Connected Home. The COVID-19 pandemic has also highlighted the growing need for increased automation for operators seeking to reduce the costs associated with sending technicians to install or reconfigure a device.
"We recognize the importance of utilizing USP and open broadband as it ensures the easy integration of productized solutions to our overall offering and allows us to reap the benefits on offer," said Jason Walls of QA Cafe and Chair of the Broadband Forum Connected Home Council. "The increase of user and vendor participation in the Broadband Forum’s Open Broadband — USP Agent project team further underlines the breadth of participation from across the industry and highlights the importance of the work being conducted."
The OB-USP-Agent project recently published its Canary release, making it easier to develop value-added services, improves remote device management security for operators, and enables integration of third-party software and services into existing gateway platforms.
Work has also started on OB-USP-Agent’s Dunlin release (Release 4), with a scope to include the completion of ‘Controller Trust’ support, the OnBoardRequest, and the ScheduleTimer mechanism.
For more information about Broadband Forum USP developments, please visit https://usp-data-models.broadband-forum.org/
About the Author: Broadband Forum is the communications industry’s leading open standards development organization focused on accelerating broadband innovation, standards, and ecosystem development. Broadband Forum is an open, non-profit industry organization composed of the industry’s leading broadband operators, vendors, thought leaders who are shaping the future of broadband, and observers who closely track our progress. Broadband Forum’s projects span across 5G, Connected Home, Cloud, and Access. Its work to date has been the foundation for broadband’s global proliferation and innovation. For example, the Forum’s flagship TR-069 CPE WAN Management Protocol has nearly 1 billion installations worldwide.
Our free technical reports and white papers can be found at https://www.broadband-forum.org/. For more information about the Broadband Forum, please go to https://www.broadband-forum.org or follow @Broadband_Forum on Twitter, and follow us on LinkedIn.
Survey: COVID-19 Pandemic Is Advancing Healthcare Technology
The COVID-19 pandemic has a majority of Americans more aware of their health and embracing health technology from telemedicine to virtual workouts, according to a new healthinsurance.com national survey of 1,000 U.S. adults.
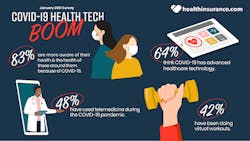
64% think that COVID-19 has advanced healthcare technology.
LIFE DURING THE COVID-19 PANDEMIC
In a health pandemic, 83% are more aware of their health and the health of those around them because of COVID-19. And that’s because COVID-19 has personally affected so many. 68% said that they have or know someone who has tested positive for COVID-19. Tragically, nearly 4 in 10 said they knew someone who passed away from the COVID-19 virus. There is a glimmer of hope on the horizon with the vaccine rollout; two-thirds said they will get the COVID-19 vaccine once available to them.
Key Takeaways
• 83% are more aware of their health and the health of those around them because of COVID-19
• 68% have or know someone who has tested positive for COVID-19
• 39% know someone who has died from COVID-19
• 64% are worried about the healthcare costs associated with contracting COVID-19
• 66% will get the COVID-19 vaccine once available to them
COVID-19 HEALTH TECHNOLOGY BOOM
64% think that COVID-19 has advanced healthcare technology and they are embracing it. 81% of those who have used telemedicine during the pandemic, said they will continue doing so once the pandemic is over. That’s a 35% increase from just six months ago.
Key Takeaways
• 64% think COVID-19 has advanced healthcare technology
• 48% have used telemedicine during the COVID-19 pandemic
• 81% will continue to use telemedicine once COVID-19 pandemic is over
FOCUSING ON PERSONAL HEALTH AND HEALTH INSURANCE IN 2021
The pandemic has many making their health a priority. 26% said they made changes to their health insurance for 2021, with the biggest reported change being increased coverage. The pandemic is also changing the way people work out. 36% said they have purchased in-home exercise equipment during the pandemic. An additional 42% said they have been doing virtual workouts.
Key Takeaways
• 36% have purchased in-home exercise equipment during the pandemic
• 42% have been doing virtual workouts
• 52% made a health-related New Year’s Resolution
• 38% already broke their New Year’s Resolution
• 26% made changes to their health insurance for 2021
• 65% of those who made changes, increased coverage for their 2021 health Insurance
• 43% of those who made changes, changed their entire 2021 health insurance plan
• 82% rate the medical and health care services they receive as good or excellent
• 41% are worried about losing their employer-provided healthcare coverage
For the entire healthinsurance.com January survey results and methodology click here.
For more information, visit healthinsurance.com.