Zero Trust – Transforming Cybersecurity
A Blueprint for Risk Reduction
When you read “Transforming” your eyes may have raised to heaven thinking it was more irritating marketing hype. However, for me, “transformation” has a specific meaning. It’s the indication of a moment of discovery that inspires and immediately creates a new way of thinking—a new future. My intention is that this article creates such a moment for you. That it’s not just informative and certainly not just more hype. Yes, it’s informative too, but let’s start at the beginning.
Multiple connected clouds, edge compute, the explosion of IoT deployment, supply chains and distributed workforces have created the cybersecurity monster. It’s able to attack a myriad of vulnerabilities. The days of the data center’s single defendable perimeter are long gone. It’s been a couple of years since John Kindervag’s Zero Trust mantras of “Assume Breach” and “Never Trust, Always Verify” became the imperative—the essential and now only viable way of ensuring that the network cloud ecosystem is secure.
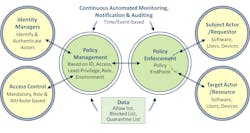
By now you likely know that Zero Trust is never a complete solution but a strategy and a set of principles. Anyone who tries to tell you that they have a complete solution is either clueless or worse. At best it might be the beginnings of a service that implements and enables some of the Zero Trust principles. (See Figure 1.)
- To enable Zero Trust principles, all users, software, and devices must be identified, authenticated, and their access limited according to the role assigned to them. Each actor must only be assigned the least privilege required to accomplish a task. I.e., accessing a limited number of functions or data and only during the assigned periods.
- They must manage and enforce and continually monitor to allow, block or quarantine access and generate notification of such events. This evolution is from the mantra to “Never Trust, Continuously Verify.” I.e., that interchanges remain verified ensuring trusted actors do not become threat actors or request out-of-policy actions.
- The principles must be applied to all exchanges between workloads, between users and providers, at distributed access points, between IT systems and IoT devices. Its purpose is not just defense against inbound attacks but also preventing exfiltration of critical data.
- Scaling via automation is essential and should be designed into products, via DevSecOps, accessed via secure APIs, ensuring all curated assets are up-to-date and avoiding human errors. The mindset should be to assume that a breach has already occurred.
- Distributed deployment is key since it must match the distributed nature of the Network Cloud Ecosystem and must reflect each enterprises requirements. In principle, it should be cautiously applied to limit processing requirements wherever a vulnerability is potentially damaging.
Zero Trust Transformative Thinking
Zero Trust’s “Never Trust, Always Verify” thinking, should not only be applied to your operational network, but everywhere! You may begin by wondering about the services and software, database systems, applications and network devices. Why should I trust them now?
What about the companies that create the products? How do I know that I can trust them? Are they using best practices suggested by this year’s White House Security Strategy?1 How can I trust the code they are using? The answer is you can’t—but you do need to hold them accountable!
This is critically important, as we saw in May’s attack in Dallas2, it applies especially to the security software and the supplying companies which the Royal Ransomware attack disabled.
A Blueprint for Risk Reduction
If this sounds hard it isn’t. In fact, here are 3 sets of best practices—effectively a Blueprint for Risk Reduction to bring order to the complexity of cybersecurity.
In order to protect user organizations, implementation of Zero Trust enabled services and products, they must be in compliance with the following protective measures applicable to their organization, product development and operation. Such compliance should be made available transparently to subscribers of such products and services.
Taking Actions to Empower Your Organization
The good news is that this thinking enables empowering actions to be performed. The 23 questions in Figures 2, 3 and 4 are examples from my Cybersecurity as a Service offering. It’s the three categories that are important. The ones about an organization will be similar but will vary by product type.
- Software and service companies that cannot give satisfactory answers to the majority of these questions are essentially “disqualified”. The scary part is that they maybe haven’t thought about them! You should not contract with them and subscribe elsewhere. In any event, your contracts/legal department should have a say. I do believe that by asking these questions you will create an important partnership with your suppliers and help them establish their own best practices to align with the 2023 US Cybersecurity Strategy.1 This is also exactly aligned to the June 2023 update from the White House4 on the Secure Software Development Framework initiative, where companies are being required to attest to their development practices.
- Conversely, end user organizations who do not ask these questions of their software suppliers, service providers, their security vendors and of their own departments are likely abdicating responsibility and will remain vulnerable or worse.
For me, this is the transformative moment that I referred to in the headline. To truly delegate not abdicate, to take control to be responsible. Now, you’ll no longer be overwhelmed by this topic. As we said, this shift in thinking is effectively a Blueprint for Risk Reduction that empowers your actions and your role!
A word on Zero Day attacks: These are attacks that have never been seen before and thus have yet to have a defense. Sometimes they get fixed by software vendors such as Microsoft, Apple and Google in regular monthly updates. Others linger for years unnoticed. They all start with the penetration of an organization then launch any number of attack types. However, if you act early and apply all the Zero Trust strategies and principles, especially the first two in Figure 4, the risk of any attack—including Zero Days—is massively reduced.
"Remember, transformative thinking creates an instant shift for your entire organization, its practices and that of your vendors, providers, contractors and supply chains to verify their operation, not to just trust them."
Keep Up Your Awareness
There are new threats developing each day. Many are multifaceted, complex, and polymorphic. “Hacking as a Service” toolkit is one ugly example of why you need to keep alert. One of many credible resources is cybyr.com. There, I’ve introduced Security as a Service with software that walks you through the process and measures your progress holistically, over time. Become a passionate student, visit my “CyberPedia” page”3 explaining 200 cybersecurity terms—many used here—and for the latest breaking news on threat detection and prevention.
Finally, don’t stress out. Zero Trust is no overnight fix. It’s a journey with the mantra “Never Trust Always and Continuously Verify”. It begins with curation of assets and services to see which, based on the financial impact, to protect first. Remember, each action you take strengthens your weakest links and reduces your risks.
REFERENCES AND NOTES
1. 2023 White House Cybersecurity Strategy: https://www.whitehouse.gov/wp-content/uploads/2023/03/National-Cybersecurity-Strategy-2023.pdf
2. Coverage of the Royal Ransomware critical infrastructure attack in Dallas, May 2023: https://bit.ly/dallasroyal
3. An annotated list of 200+ terms are explained at https://cybyr.com/cyberpedia.
4. White House update on self-attestation in its Secure Software Development Framework: https://bit.ly/whjune23
About the Author
Mark Fishburn
Provider of Strategic Network, Cybersecurity, Software, and Marketing Services
Mark is President of cybyr.com and has five decades of experience in software, networking, and security. He is a member of ONUG, Mplify, and CSA network and security working Groups, CISA contributor and publisher of the Holistic Cybersecurity book: Hey Who Left The Back Door Open? For more information, or to give feedback, email [email protected] or follow him on LinkedIn.