Assume Breach – Now What?
What's this about?
IN 2025, RANSOMWARE is still running rampant, threatening everyone who reads this. Today, Zero Trust is the accepted strategy for protecting organizations and individuals from cybersecurity threats. Defenses are built around two principles: “Never Trust, Always Verify” and “Assume Breach.” The first focuses on prevention: identifying and authorizing access to data, applications, and networks as do thousands of products, many based on the NSTAC1 five-point implementation plan.
On the other hand, “Assume Breach” implies that your defenses may have already been breached, and the enemy is working inside your ecosystem. I realized that there was a game-changing opportunity for service providers to detect and curtail ransomware breaches for their customers inside their network as a massive business advantage. It happens inside the provider’s network—that’s what this article is about.
Ransomware as a Service delivers what is known as an Advanced Persistent Threat (APT) attack. This is a sophisticated, often complex and sustained cyberattack that is today’s principal vehicle for ransomware.
Today, the ubiquitous use of multiple and hybrid clouds and the growing importance of wide area networks, internet access, and distributed workforces has significantly increased the attack surface. The relevance being that attacks and breaches span and are therefore detectable via the connecting services such as Network as a Service (NaaS) and SASE.
My article2, in ISE Magazine’s November/December 2024 issue, described multi-layer defenses. This article deals exclusively with how detection and removal of breaches can empower service providers. It explores the nature and detection of these activities to circumvent highly visible ransomware attacks where breaches have occurred—an area that has received (perhaps shockingly) very little attention.
It shows how service providers, including MSPs and SASE providers, now have the opportunity to play a strategic role in the prevention of ransomware. It’s about using Zero Trust techniques with the detection and removal of such attacks where defensive measures have failed. Its scope is to list the necessary steps required to implement such a strategy. As with all cybersecurity actions, the more weak links you strengthen, the more your risk is reduced.
Ransomware as a Service – The Threat Actors Killer App
It’s important to understand the nature of such attacks and why, what, and where this approach works.
Ransomware attacks are most often enabled by the use of “Ransomware as a Service” (RaaS)—effectively a for-purchase platform to deliver such attacks with limited technical knowledge required. As opposed to malware, which typically acts immediately, RaaS delivers what is known as an Advanced Persistent Threat (APT) attack. This is a sophisticated, often complex and sustained cyberattack that is today’s principal vehicle for ransomware. This platform typically delivers attacks that consist of techniques for:
- Initial penetration to create a breach. Many techniques. With 80+ threat types and 40+ defensive actions, it is inevitable that mitigating actions are missed, and breaches occur.
- Infiltration and discovery of vulnerabilities, deployment of malware in network-connected systems—central to this article.
- Corrupting or exfiltrating information—what we are ultimately preventing.
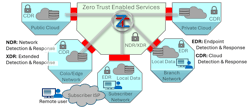
Breaches can occur within subscriber (end-user) systems, in multiple clouds and remote user systems. Increasingly the transactions between subject and target actor span wide area networks including NaaS and SASE services.
From Figure 1 below, it becomes obvious that when a breach occurs, it’s the network service that is ideally placed to detect the signs of such a breach using Zero Trust security functions to disable them.
Ransomware Detection and Removal
The initial penetration of an APT begins with reconnaissance of the end-user system including identification of vulnerabilities, employee credentials, hiding of malware through phishing and insider threats. This is followed by penetration of native software systems, known as “living-off-the-land attacks.”
Next comes malware, the use of identity theft to elevate the privilege to discover network-connected software and data.
Then, transactions must run the gauntlet of the network services. This is where systems in the network software can identify suspicious and out of policy actions and block them.
Zero Trust Architecture That Enables Breach Detection
It’s recommended to begin with the study and implementation of three security standards developed by MEF3. These are MEF 118.1 Zero Trust Services Framework Attributes, MEF 138 Security Functions, and MEF 117 SASE Services. This author has been personally contributing to the work over the last four years. When implemented and deployed they present an important security foundation for this work.
Applying Zero Trust to Nullify Threats
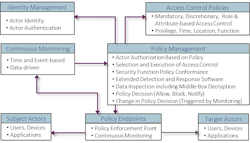
Figure 2 below shows the Policy Management steps that authorize actor transactions. This includes how they are identified, authenticated and that the types of transactions are aligned with policy, privilege, etc., as appropriate for every point where the policy is enforced. The following covers how services implementing Zero Trust attributes and related security functions fit together. Verification that supporting software and applications transmitted are malware-free are additional important elements.
Detectable Network Transactions
There are some telltale signs. Actions such as “Beaconing” (attempts to communicate the threat actor’s host software) are easy to spot. Lateral Movement to infiltrate connected systems embed malware can be detected by registering legitimate users and software, etc. While encrypted transfer of data is detectable by a middle box function, recursive encryption used by threat actors is not but can be blocked. An important addition to detection of breaches is the use of Extended Detection and Removal Software that is not covered in the MEF specifications. In all cases software supplied by third parties must be verified rather than trusted.
Something’s wrong, something’s not quite right. When a transaction is obviously “wrong” or not at the right time, from the right location, etc., it can be blocked, quarantined, and investigated.
What Actions Should You Take Next?
Clearly, there are too many threats and defenses to be covered in this article. Here we just created the framework. Next steps are to visit my website. There the story goes into detail on the specifications, links to MITRE ATT&CK threats and provides further descriptions of the security functions. The place to start? Cybyr. com/assumebreach.
As indicated, there are many aspects of the enterprise ecosystem that can be affected: subscriber networks and systems, and cloud infrastructures where Endpoint and Cloud detection software can be used to detect breaches. This article does not let the end users off the hook either since almost any system can be breached. Full Asset Protection, business resilience and holistic cybersecurity cannot be ignored. I hope this was not too complicated to take on because the payoff is huge. To that end, we created our Virtual Cybersecurity Officer Service (cybyr.com/vcso) so we can help you implement the approach and reduce your risk and that of your customer/clients, measure your progress, and help banish the threat of ransomware.
Vigilance
Finally, continual awareness of development in attack techniques and defensive responses remains an essential part of every cybersecurity strategy. Any questions, please contact me at linkedin.com/in/markfishburn/.
-
NSTAC: The President’s National Security Telecommunications Advisory Committee 2022, tinyurl.com/ZT-nstac22
-
ISE Magazine: Have Your Security Thrive in ’25, isemag.com/55235575
-
MEF Security Specifications, mef.net/service-standards/cybersecurity-services
All terms used here are explained at cybyr.com/cyberpedia. The extended version of this article is located at cybyr.com/assumebreach.
About the Author
Mark Fishburn
Provider of Strategic Network, Cybersecurity and Marketing Services
Mark Fishburn | Provider of Strategic Network, Cybersecurity and Marketing Services.
Mark is CEO of cybyr.com and has five decades of experience in software, networking, and security. He is a member of ONUG, MEF and CSA network and security working Groups, CISA contributor and publisher of the Holistic Cybersecurity book: Hey Who Left The Back Door Open? For more information, or to give feedback, email [email protected] or follow him on LinkedIn.