How to Improve Your Supply Chain Stability
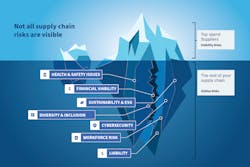
Today, telecom/ICT leaders worry about multiple risks related to health and safety, workforce management, sustainability and ESG, diversity and inclusion, liability, financial viability and cybersecurity. While these are concerns across the industry, most providers are challenged to understand the subtle and not-so-subtle risks of their supply chain.
In fact, most organizations have the means to focus only on top-spend suppliers, missing significant and unseen risks from smaller suppliers in other areas of the supply chain. Those risks can be costly at $47,000 per accident, up to $1 million per day per environmental violation and $4.2 million per cyber incident and more.1
While your company may have a policy that promotes inclusion, it’s nearly impossible to Google search a minority-owned business within 40 miles of a cell site near Atlanta that can do preventive maintenance on the site’s fans, seals, cables, connections, and batteries.
While many solutions exist to manage these risks separately—whether by spreadsheets, siloed documentation, etc.—supply chain risk management (SCRM) technology is now helping companies focus on leading indicators and proactively manage risks through a holistic view of the entire supply chain from your largest to the smallest, most specialized supplier. SCRM technology helps companies manage supply chain risks and their suppliers to become more qualified for jobs. It provides a more holistic view of supply chain risks across many different risk categories.
SCRM Technology enables a four-step process to manage your risks:
- Tracking all your suppliers
- Ensuring they are compliant
- Verifying they are compliant, including the workers
- Discovering new suppliers that meet your company’s criteria
Here’s how those steps are applied across six major areas of risk that telecom providers and their suppliers face.
1. Health and Safety
As ISE readers know, the telecom industry can be extremely dangerous because of tower climbing and the remote nature of the work. Plus, companies are under a lot of pressure to create the infrastructure to meet the demands of installing and maintaining 5G and other advances in technology. A recent Avetta survey found 79% of executives consider employee health and wellness as “very important”.2
A company needs to have the training and policies in place to make sure their employees are healthy and safe. But how can this be monitored in real-time if those standards are not being met by outside contractors and subcontractors? SCRM technology ensures they have the training, certifications and safety record needed to uphold the health and safety requirements of your organization.
2. Workforce Management
The telecom industry had remote workers in the field long before remote work was normal. Field techs can be working across many locations. Some must even do their work underground, in customers’ homes and/or on wireless towers. Their managers may be alongside them at times but likely in offices far from their team more often. Field techs, installers, and contract supervisors must be competent in a wide range of areas. And their leaders must have visibility and transparency to know the level of competency for every worker.
Your company may have highly defined policies related to employees accessing sensitive equipment and workplaces. But does it have the right technology in place to ensure every contractor and subcontractor has the proper certification, training, and insurance before they work in sensitive areas or with specialized equipment?
While it’s important to make sure all the documentation for each company and worker is in order, you can take it a step further with on-site verification—boots on the ground to evaluate performance. Someone should be physically present to audit and confirm that workers trained in a certain aspect of work can competently perform that work. Then, document that verification so it’s visible across the supply chain and across projects.
Verification is especially important with the tight labor market, making sure workers are operating according to the latest standards for their clients. Feedback from the verification process is also important for suppliers and contractors. They can improve their processes and expertise through these audits.
3. Sustainability and ESG
Regulators, shareholders, and the public now demand organizations place a high priority on the Environmental, Social and Governance (ESG) aspects of corporate practices. Up to 90% of a company’s environmental footprint can be in its supply chain. The survey referenced above found that while most executives list managing and reducing a company’s environmental footprint as “very important” to the organization, only 39% list ESG supply chain issues as “very important”. Even though there are fewer respondents who say ESG is very important, 83% of their organizations have ESG supply chain plans.
The following steps can help meet your organization’s ESG goals:
- Set internal ESG targets.
- Adjust sourcing and procurement policies to align with the organization’s ESG policy.
- Engage with suppliers on improving ESG performance.
- Join industry/sector networks to support and develop supplier education and best practices programs.
4. Diversity and Inclusion
Companies are being asked to have diverse, local, and sustainable suppliers. They also must have a backup plan for unseen needs. While your company may have a policy that promotes inclusion, it’s nearly impossible to Google search a minority-owned business within 40 miles of a cell site near Atlanta that can do preventive maintenance on the site’s fans, seals, cables, connections, and batteries.
In fact, most organizations have the means to focus only on top-spend suppliers, missing significant and unseen risks from smaller suppliers in other areas of the supply chain. Those risks can be costly at $47,000 per accident, up to $1 million per day per environmental violation and $4.2 million per cyber incident and more.
5. Liability and Financial Viability
Telecom companies can often be the target of lawsuits and fines due to the actions of contractors and subcontractors. That’s why you need to understand the history, current practices, and the amount of insurance carried by suppliers, contractors, and subcontractors. In order to make sure your business is sustainable, be sure to learn that your suppliers and contractors have the financial stability necessary to stay in business for the long-term.
6. Cybersecurity
The Brooking Institution notes the telecom industry is very prone to cyberattacks because companies collect, share, and transfer massive amounts of information about their customers.3
These businesses need robust privacy and access rules. Because of the absence of government regulations, the think tank notes telecom companies have a very difficult time preventing privacy abuse by suppliers, third-party providers, and contractors. Your company needs to have guardrails and enforcement in place that prevent malware attacks, data breaches, surveillance and economic espionage for both your company and its suppliers.
Final Thoughts
Today’s telecom executives face countless risks from their employees, contractors, subcontractors, and suppliers. Oftentimes, their best intentions to manage risks are disparate documents including spreadsheets, forms, and disconnected systems that don’t talk to each other.
Telecom leaders should leverage newer SCRM technology to systematically track, verify, and identify needs across their organization. This is the best way to keep their business and supply chain sustainable from top to bottom.
RESOURCES AND NOTES
1. Data from the National Safety Council (NSC) Slips/Trips/Falls calculations, Resource Management Associates research, and supplier support, document collection & verification, compliance assessments & corrective actions costs.
2. https://www.avetta.com/sites/default/files/2021-05/Avetta_ESG%20White%20Paper_Open%20File_compressed_0.pdf
3. https://www.brookings.edu/blog/techtank/2022/01/19/protecting-national-security-cybersecurity-and-privacy-while-ensuring-competition/
About the Author: Scott Spencer is Senior Vice President of Global Strategic Accounts at Avetta, a global leader in supply chain risk management tools. Scott has been a member of the Avetta team since its inception in 2003. He has served as commercial director of global development and director of sales (Americas), utilizing his diverse experience in international markets to understand and thrive within the changing landscape of health and safety. For more information, please email [email protected] or visit www.avetta.com/resources. You can also follow Scott on Twitter @Scott_Avetta.
Follow Avetta on:
LinkedIn: https://www.linkedin.com/company/avetta/
Facebook: https://www.facebook.com/AvettaNews
Twitter: https://twitter.com/AvettaNews
YouTube: https://www.youtube.com/c/AvettaNews
Instagram: https://www.instagram.com/avettanews/
About the Author
Scott Spencer
Senior Vice President of Global Strategic Accounts
Scott Spencer is Senior Vice President of Global Strategic Accounts at Avetta, a global leader in supply chain risk management tools. Scott has been a member of the Avetta team since its inception in 2003. He has served as commercial director of global development and director of sales (Americas), utilizing his diverse experience in international markets to understand and thrive within the changing landscape of health and safety.