Latest from Network Transformation/Edge Compute/IoT/URLLC/Automation/M2M
Tackling Network Transformation
A Method for Your Madness —
Access network architectures, designed to funnel data from very many end points to a convergence point, are fundamentally different from any other network architecture. Moreover, while demand growth is the key transformation driver for most of the network, it is only one of the factors triggering change in the
access network.
The service that can be offered to a subscriber is directly related to the capabilities of the access link connecting the subscriber. For example, if you want to increase the maximum bandwidth tier from 100 Mbps to 1 Gbps, the access link needs to be able to peak up to 1 Gbps even though the change may only have a minor impact on the average bandwidth consumption and thus not impact the rest of the network.
Hence any corporate decision to change service offerings or customer connectivity options (e.g., corporate decision to connect all Multi-Dwelling-Units with fiber for competitive reasons) directly impacts the access network and drives frequent, sometimes non-linear, upgrades.1 Add in the continuous need for new access links to serve greenfield areas, new subscribers, or new service end-points, and you understand why the access network needs constant attention.
Clearly, access transformation planning is much more than a simple growth-based upgrade optimization exercise. Given the number of triggers for change and the uncertainty of all inputs,1 tackling the access network transformation challenge can be successful only by evaluating and comparing a significant number of transformation alternatives.
4 Steps for Your Future
For this to be feasible in a short amount of time, an access-domain-specific methodology is needed to automate the heavy lifting of creating an access network transformation plan. This article lays out 4 high-level steps in an access domain network planning methodology.
Step 1. Understand how access networks can evolve.2
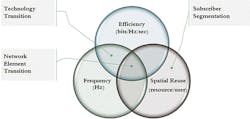
For any access technology, the link capacity per subscriber is defined by 3 components, as shown in Figure 1: spectrum bandwidth, spectral efficiency, and how many end point (subscribers) share the capacity.
Figure 1. Transformation Action Basics
In access networks, only 3 types of upgrade actions are used to improve on one or more components:
1. Technology Transitions = Upgrading the technology of a link to a newer member in the technology family
(e.g., ADSL to ADSL2): typically improves the available spectrum as well as the spectral efficiency.
2. Subscriber Segmentation = Redistribute subscribers on more access links, resulting in more bandwidth per subscriber.
3. Network Element Transition = Move subscribers to a different access network element. This is typically done for one of the following reasons:
• Shorter distance: Using higher spectrum bands on the access link can negatively affect the distance the signal can reliably propagate, forcing the active access network element to be placed closer to the subscriber.
• Redistribute subscribers: Segmenting shared media often goes hand in hand with moving subscribers to new smaller network elements, typically placed closer to the subscriber.
• Move subscribers to a new technology family: For instance, changing subscribers for a copper to fiber access technology.
InvisiLight® Solution for Deploying Fiber
April 2, 2022Go to Market Faster. Speed up Network Deployment
April 2, 2022Episode 10: Fiber Optic Closure Specs Explained…
April 1, 2022Food for Thought from Our 2022 ICT Visionaries
April 1, 2022Step 2. Model upgrade paths, triggers, and constraints.
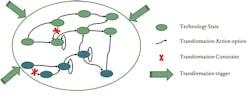
From Step 1, it’s clear that increasing bandwidth capacity of an access link comes down to making changes to the access network element the subscriber is connected to. At any given point in time the access links of a network element are in a specific technology state (e.g., "GPON state"). Therefore, modelling all potential upgrade paths for an access network can be simplified to identifying the upgrade options for each technology state unlocking the key to a straightforward automation algorithm.
See Figure 2: Instead of specifying complete paths such as: ADSL-> ADSL2 -> FTTN VDSL -> Sealed remote VDSL2 -> …, and ADSL -> ADSL2 -> GPON -> XGS-PON, you simply specify options for each state
(e.g., ADSL2: option 1 FTTN VDSL, option 2: GPON).
Figure 2. Modeling Transformation Behavior
The second part is to model when network elements need to upgrade out of a technology state. A network element is triggered for upgrade either by running out of capacity because of user demand growth or to accommodate policy and service decisions. Growth triggers can be easily modeled by creating profiles defining how subscriber demand is growing year-over-year. This allows an execution engine to calculate the predicted demand at any point in time, and trigger an upgrade if a threshold percentage of technology capacity is exceeded. Policy and service trigger modelling simply comes down to defining when and under what condition an upgrade action will be forced (e.g., in 2020, force fiber to the building for all MDU customers).
Lastly, to really have full flexibility in modelling transformation behavior, constraints can be added to the model, specifying conditions when potential upgrade options are not available (e.g., in market "A", prevent all copper-based upgrade options starting Q2 2021).
Step 3. Calculate transformation actions.
With the upgrade behavior for a network element at a given point in time (modeled in Step 2), the algorithm to calculate all transformation actions required to keep the access network compliant for an arbitrary time-scope (e.g., 10 years quarterly, 5 years monthly) becomes trivial. Simply start with the current state of the network elements to be analyzed (use either details of real brownfield network or a made-up representative architecture if details are not available). For every calculation period, execute the following actions as shown in Figure 3:
• Add new network elements needed for network expansion. (To understand how to define network expansion with or without details, see source noted in (3).)
• Follow Figure 2 behavior rules to calculate all active network elements to calculate resulting state or new network elements.
• Use resulting network state as input for next calculation period, and repeat.
The result of this process will include a detailed view of the network state over time, and all transformation actions at the individual network element level.
Figure 3. Transformation Calculation
Step 4. It all comes together.
Step 3 completes the methodology to calculate an access network transformation plan for a set of assumptions. That is great — but unfortunately, not very useful. To assess the value of a plan, much more information is needed. You must understand if the plan is implementable, and be able to compare and contrast different plans. Additional information that any planning method should provide includes: detailed cost over time, labor and material resource requirements over time, construction activity over time, and much more.
Luckily all this information can be defined for each type of upgrade action. The methodology already calculates individual actions for specific network elements at defined points in time. All the required details can be easily calculated from the upgrade action definition combined with network element attributes such as household passed, household connected, access and feeder miles, etc.
And what about costs that are not related to upgrade activity, such as network operations cost? OpEx cost is typically linked to active subscriber count and the access technology used. Since the methodology already identifies the technology state and subscriber count of all access network elements and any point in time, OpEx calculation becomes a straightforward addition.
This methodology for even a medium-size access network will create millions of data points. To turn all this data into useful decision-driving information, the results need to be presented in a visualization tool with a template, giving immediate enterprise level insights with the ability to zoom into the individual network element, specific period, and individual component.
Worth the Effort?
Obviously, reducing network transformation analysis time from weeks to hours is in itself a large value. More importantly, not being limited by the amount or complexity of access transformation alternatives that can be analyzed in a timely manner is an immeasurable benefit.
And there is more! Once a framework based on this methodology is in place for a network, it makes answering the smaller questions that come up all the time trivial. Some examples include:
• What technology/ architecture should I use for a new greenfield area?
Answer: Run your scenarios for the greenfield footprint, and in minutes you’ll have the best future-safe option.
• Competition is rolling out 1Gbps service in city X. What will it take for me to counter?
Answer: Add the rule to all your scenarios and run for city X to get your best option.
• Do I have the budget and resource to roll out fiber to all MDU customers in market Y?
• What if …? Answer all of them in a timely manner, and with minimal effort.
Remember: lacking some details on your current network architecture is not a showstopper. The methodology can be used to understand the impact of new technology options and/or strategic directions starting from a high-level characterization of the existing network. The latter makes the methodology indispensable in all phases of the access network transformation decision-making process.
Like this Article?
Subscribe to ISE magazine and start receiving your FREE monthly copy today!
Endnotes
1. Rajesh Abbi, Luc Absillis, Sudheer Dharanikota, "Brownfield Broadband Access network planning in a rapidly changing environment", 1Q 2019. https://www.firstprinciplesinnovations.com/whitepapers/brownfield-broadband-access-network-planning-in-a-rapidly-changing-environment/
2. Absillis, "Access Transformation – Technology Basics", Broadband Library, September 2018. https://broadbandlibrary.com/wp-content/uploads/2018/09/FirstPrinciples-Fall-2018-WP-Image.pdf
3. Absillis, "Solving the Access Network Footprint Expansion Enigma", 2Q 2018. https://www.firstprinciplesinnovations.com/whitepapers/solving-the-access-network-footprint-expansion-enigma
If you’re intrigued with the process described in this article, you can find detailed background at First Principle Innovations (http://www.fpinno.com). Check out AP-Jibe, a fully flexible access network transformation toolset that implements this methodology and much more. For more information, please email Luc Absillis: [email protected].