Latest from Network Transformation/Edge Compute/IoT/URLLC/Automation/M2M
Cybercrime and the Internet of Threats —
A new report by Juniper Research, Cybercrime & the Internet of Threats 2018, found that over 33 billion records will be stolen by cybercriminals in 2023 alone, an increase of 175% over the 12 billion records expected to be compromised in 2018, resulting in cumulative loss of over 146 billion records for the whole period.
The new research found that, in spite of legislation like GDPR and PSD2 mandating strong cybersecurity and authentication measures to protect personal and financial data, average levels of cybersecurity spend will remain relatively static.
Cybercrime is a growing threat to corporations and consumers, who are increasingly using online methods to run their businesses and lives. The research presents the latest observable trends in cybercrime, as well as indicating the potential global cost of malicious software use.
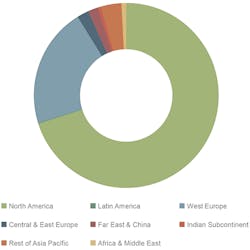
We expect over 146 billion records to be exposed through criminal data breaches between 2018 and 2023, growing at a rate of 22.5% per year. Note that this is actual data breaches, not just reported data breaches. We have assumed that an increasing proportion of data breaches will be reported thanks to tightening cybersecurity legislation, reaching nearly 90% of all breaches made in 2023. (See Figure 1.)
• The lowest areas for reporting breaches will be much of Rest of Asia Pacific, which has little in the way of mandatory reporting requirements, and Japan, where cultural predilections will overrule the disclosure requirements, helped by low fines.
• The US will remain the largest single target throughout the forecast period, as this is the location of the most valuable data for cybercriminals, as well as a common location for global corporate data hubs.
Figure 1. Cybercrime Breached Records Volume, Cumulative Total 2018-2023, Split by 8 Key Regions: 146 billion (Source: Juniper Research)
Spend by small businesses in 2018 will make up only 13% of the overall cybersecurity market in 2018, despite over 99% of all companies being small businesses. In addition, the cost of breaches can exceed millions of dollars, dwarfing the turnover of such businesses.
Many of these companies use consumer-grade products, spending on average under $500 per year on cybersecurity. With many such businesses digitizing, this will leave them vulnerable to newer forms of malware which require more advanced cybersecurity, beyond simple endpoint protection.
5 Cyberthreats to Watch
Peak Ransomware: This was detected in record numbers at the beginning of 2017, largely due to the success of the Ransom.AndroidOS.Congur Android ransomware and WMI-based ransomware like WannaCry. However, the majority of this activity was at the beginning of the year, with few updates being applied to known ransomware families as the year moved on. This is because cybercriminals are now finding other means to monetize device capture, without requiring the compliance of an end user, which is rarely given.
Malvertising: While adware has been a persistent subtype of malware through its annoyance value, 2017 was the year malvertising became a more persistent problem. This has grown into a platform where cybercriminals now create fake advertising companies to host malware-ridden ads.
These can then be spread through interaction with legitimate online ad agencies and content distributors. They typically contain an array of forced redirects which then deploy the actual malware. In addition to this, malvertising also frequently functions as a vector for the deployment of cryptojacking malware.
Cryptojacking Emerges: With ransomware not as lucrative as it once was, some cybercriminals are switching to cryptojacking, as the pay-off is more predictable. This can be easily deployed in a few lines of code into a browser and then inserted into an operating system through an automated JavaScript execution.
Creating botnets out of corporate infrastructure to mine cryptocurrencies has also become popular. While Bitcoin was once the reimbursement of choice for cybercriminals as ransomware, the factors mentioned below are driving cybercriminals to alternative currencies (altcoins), most particularly Etherium and Monero.
Thanks to the evolution of cryptojacking and ransomware, a new Rahkni ransomware variant has now emerged which selectively chooses whether to install ransomware or a cryptojacker, depending on the host machine’s configuration.
Fileless and Userless Malware Comes of Age
In 2017, many of the most severe attacks (including WannaCry and NotPeyta) did not install malicious programs but instead co-opted PowerShell, Windows Management Instrumentation (WMI), Windows Credentials Editor (WCE) and Group Policy Objects (GPO). These tools are generally used to manage networks, so their interaction with endpoints is expected. It is also generally not done at the initiation of the endpoint user either, as they perform scheduled maintenance tasks. These tools are now becoming a focus for malware, and the most prolific ones to date have utilized the EternalBlue WMI vulnerability (CVE-2017-0144).
These can be remedied to an extent by limiting or disabling WMI and PowerShell services when they are not in use, as well as the use of traditional attack vectors like macros, which are now evolving fileless variants. Network behavior analysis is another tool that will catch these attacks where traditional measures will not, as it looks for activity patterns rather than specific files.
InvisiLight® Solution for Deploying Fiber
April 2, 2022Go to Market Faster. Speed up Network Deployment
April 2, 2022Episode 10: Fiber Optic Closure Specs Explained…
April 1, 2022Food for Thought from Our 2022 ICT Visionaries
April 1, 2022We therefore believe that the most successful cybersecurity businesses, regardless of their area of focus, will be those who partner with other entities to combine the different elements of cybersecurity into an integrated system.
While several different kinds of cybersecurity products can co-exist, they create a situation that is difficult to manage for end users, resulting in the possibility that threats may be missed.
While Security Information and Event Management (SIEM) systems exist to manage and, to a degree, aggregate these issues, the product range is still fragmented, with comparatively few truly integrated solutions compared to the range of single-purpose cybersecurity products available. This approach, the desire for the best-in-class solution for each specific problem, is being increasingly questioned by cybersecurity professionals. It severely complicates cybersecurity workflows, in addition to potentially producing multiple truths where areas of competence overlap. The sector needs managed solutions and software suites that effectively integrate and interpret these diverse tools, to make existing workflows more efficient.
The latest National Institute of Standards and Technology (NIST) specifications have begun a move to a common language for describing cybersecurity threats, which will go some way toward easing this problem.
It will also make finding holes in existing infrastructures easier through the use of a common frame of reference. However, as the NIST framework is not mandatory it will take some time to reach a point of ubiquity, if it does at all.
Deception Technologies on the Increase
Deception technologies, which provide spoof information for malware to execute on and do no damage, while also triggering an alert to cybersecurity teams, is becoming more popular. Now that the technology has evolved beyond simple honeypot deployments to a range of possible deception types, it can be used by many different enterprises.
However, despite growing interest in the space, deception technologies, at their base, simply create more alerts. Both end users and deception technology vendors need to have a plan for what to do with the information that deception technology provides, and how it is implemented in a broader cybersecurity strategy. If this is not communicated, customers may end up dissatisfied with the product and, at a broader level, many in the market may consider deception technology useless.
Mandated Cybersecurity and Regulation
Several regulatory instruments, from General Data Protection Regulation (GDPR) to Payment Services Directive 2 (PSD2), all require high standards of cybersecurity. From a compliance perspective, building secure systems and data storage is fast becoming table stakes for doing business online. Accompanying these regulations are hefty fines for non-compliance with procedures in the event of a data breach.
Thanks to these regulations, companies are already facing fines for not disclosing data breaches. There are moves in the UK to introduce a liability shift for consumers who fall victim to phishing scams, and other initiatives may follow. If applied to data breaches, this would correct a longstanding cybersecurity moral hazard; that the companies do not necessarily suffer directly from a data breach involving customer data. Such a liability shift would also standardize the growing cyberinsurance industry, giving a clearer object for their coverage.
Given the readier appetite for regulation, we expect such directives to come first from Europe, although several landmark cases in the US over the past few years may establish a de facto liability shift based on precedent.
The white paper Cybercrime & the Internet of Threats 2018 provides a summary of the latest cybercrime threats, an analysis of the current state of key segments of the cybersecurity market and a forecast for future data breach volumes. For more information and to download, please visit https://www.juniperresearch.com/document-library/white-papers/cybercrime-the-internet-of-threats-2018.